OverviewCopy link to clipboard
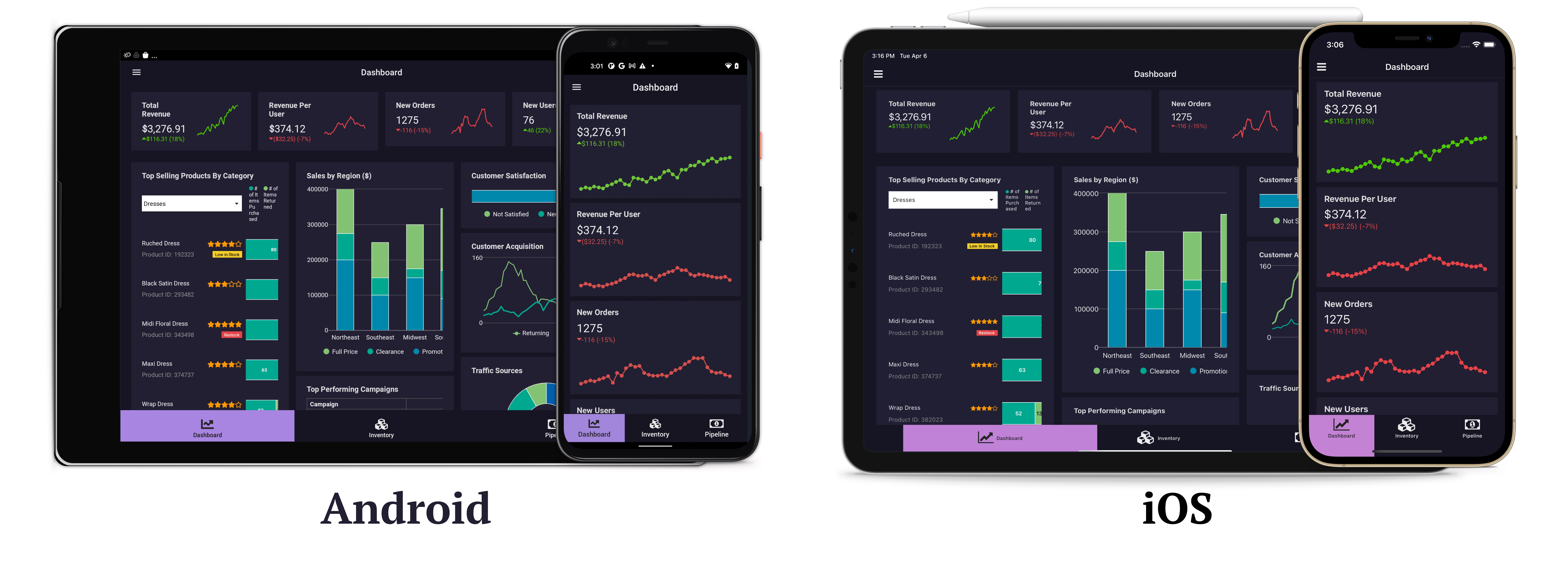
Appian Mobile enables users to monitor, collaborate, and take action on the go by providing access to task and event notifications, up-to-date business information, and ad-hoc collaboration, all from the convenience of their iOS and Android devices.
All you need to do to begin working with Appian Mobile is download the app from the iOS App Store or the Google Play Store and create your account.
Note: Appian Mobile relies on mobile operating system features to secure data within the Appian application. Customers who require strong assurance of confidentiality between users should not allow users to share the same mobile device, particularly if they are utilizing offline mobile features.
See also: System Requirements for Mobile devices
Appian for enterprise mobility managementCopy link to clipboard
Enterprise mobility management (EMM) is a way for organizations to control and secure the mobile devices used by their employees. EMM practices help keep company data safe and secure while still allowing employees to work on the go as needed. See Appian for Enterprise Mobility Management (EMM) for more information.
Custom mobile applicationsCopy link to clipboard
Administrators and developers can customize different aspects of Appian Mobile to create a different look and feel that mirrors your organization's style in end-user interfaces. See Custom Mobile Applications for more information.
Network communication requirementsCopy link to clipboard
The Appian Mobile application must have access to the Appian server. See Mobile Authentication Requirements for more information.
Hardware recommendationsCopy link to clipboard
We recommend that users access Appian Mobile using mobile devices with a minimum 4 gigabytes (GB) of RAM. Depending on your Appian Mobile use case, you may want to use mobile devices with higher RAM, such as 8 GB, to support the needs of your applications.
For example, we recommend using mobile devices with more RAM if using Appian Mobile for a use case that includes any of the following:
- Offline mobile.
- Many file upload components on an interface.
- Many images on an interface.
Client authenticationCopy link to clipboard
Appian Mobile supports Appian, LDAP, and SAML authentication mechanisms. It does not support SAML IdP-initiated sign in or client certificate authentication (CAC/PIV, smartcard).
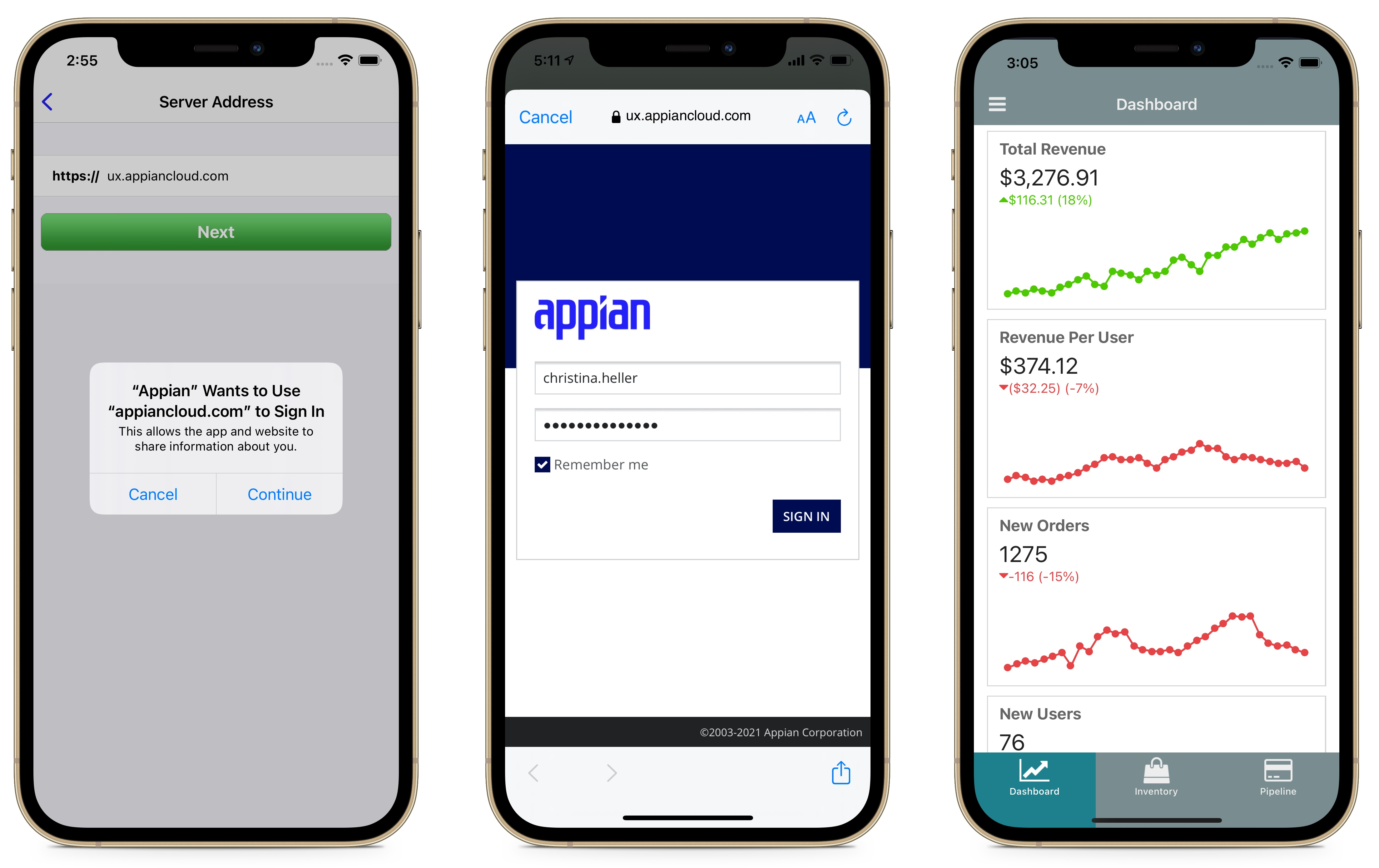
When creating an account the mobile client presents the appropriate sign in screen to the user in an in-app browser. After users have successfully authenticated from the in-app browser, they are automatically redirected back to the mobile application. Users are required to go through this sign in workflow every time their session expires. Session expiration is controlled by the Appian server's authentication layer.
When a user signs in to Appian Mobile on an iOS device, the operating system will prompt them to grant the application access to the site’s data in Safari.
Client Certificate AccessCopy link to clipboard
With client certificate access, users can import a certificate into the mobile app. The certificate is used to ensure that access to the Appian server on the organization's internal network is restricted to clients that can provide a valid certificate when presented with a certificate challenge.
The validity of the digital certificate is typically ascertained by a network security service (gateway) that is responsible for keeping out unauthorized traffic from the organization's network.
The feature can be enabled on Appian Mobile applications deployed through an enterprise mobility management provider using a custom configuration. When enabled, the option to import a certificate into the mobile app is made available on the Accounts screen.
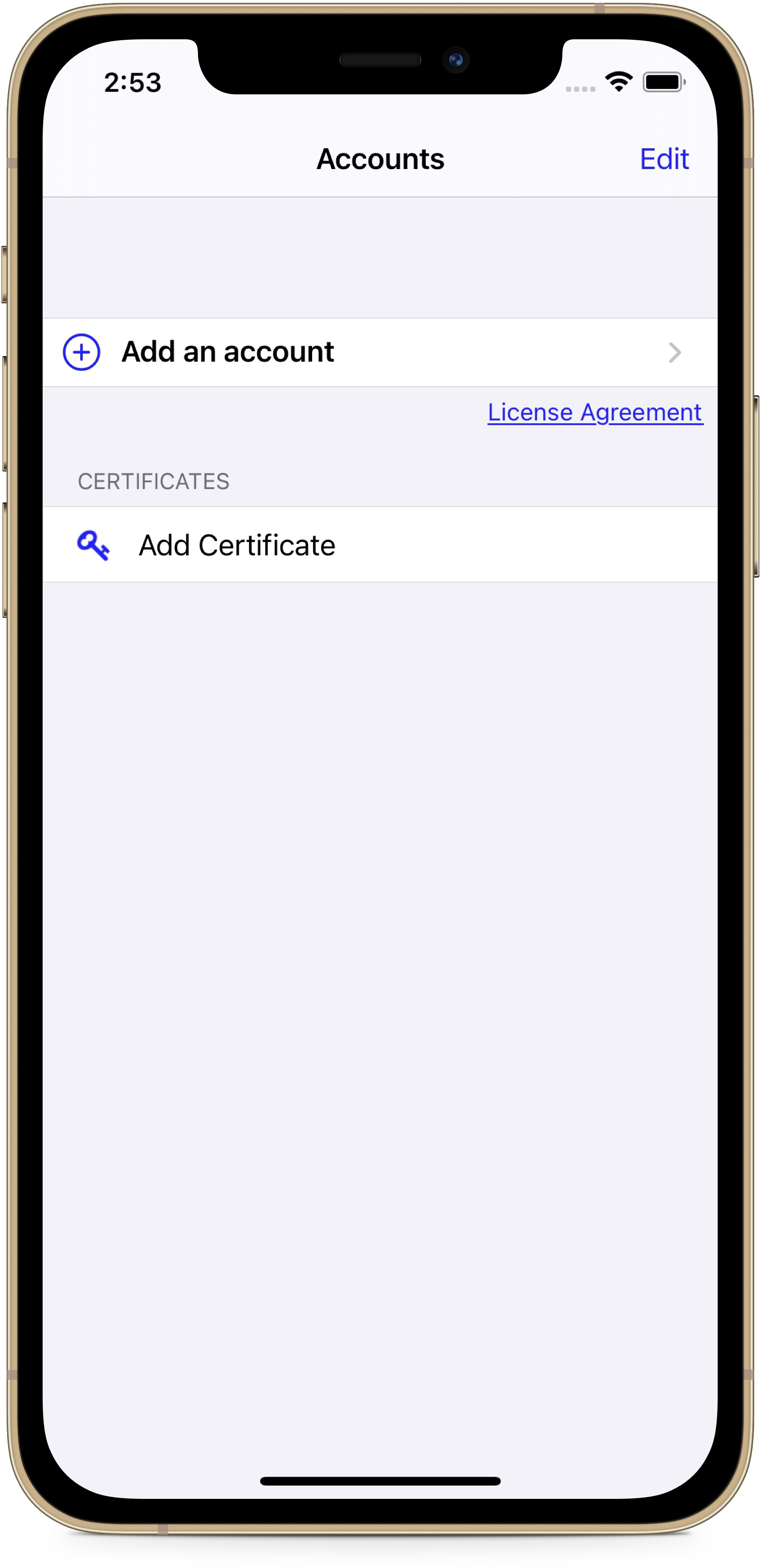
For the Appian Mobile iOS application, the certificate can be imported from any application that acts as a Document Provider. For the Appian Mobile Android application, the certificate can only be imported from the device's trusted credential store.
The imported certificate is automatically presented by the mobile app any time it receives a certificate challenge. After validating the certificate, the gateway forwards mobile app requests to the Appian server.
Derived credentialsCopy link to clipboard
Client Certificate Access can also be used to access derived credentials (certificates derived from user's smart card credentials) deployed by providers like Purebred, used by the Department of Defense (DoD).
Tip: Purebred is a managed registration service to deploy and configure user certificates on mobile devices. Similar to using a common access card (CAC), mobile devices enrolled using the Purebred registration process can be used to perform security functions on DoD information systems such as authentication, authorization, and generation of digital signatures.