If you have special network configurations and are using Appian Mobile, it is important to understand how the mobile application authenticates with the Appian server, so that your users are able to seamlessly use the application. This page explains how mobile authentication works, the network requirements, and the supported methods for restricting access to the Appian server.
To understand Appian Mobile's network requirements, it helps to understand how the client and server communicate during mobile authentication.
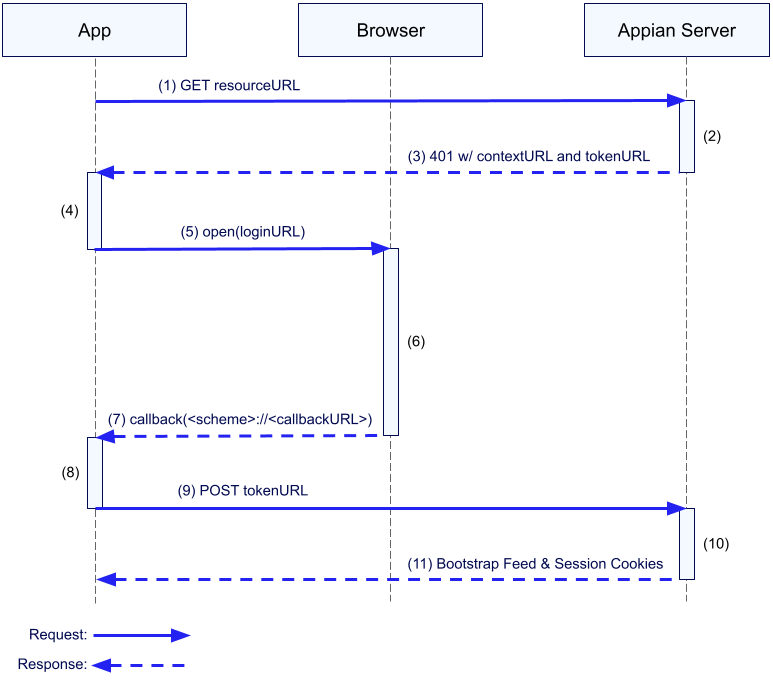
1
2
3
4
{
"contextUrl": "https://mysite.appiancloud.com/suite",
"tokenUrl": "https://mysite.appiancloud.com/suite/mobileAuthTokenConsumer"
}
contextUrl and tokenUrl keys and came from an Appian server.1
https://mysite.appiancloud.com/suite?codeChallenge=zWNaqbvS3TXav7Kq4TNtwT196dIIB3yS50JG2TrzKkQ&scheme=com.appian.tempo
1
com.appian.tempo://mysite.appiancloud.com/suite?result=login&token=jA0ECQMC1PKb87zVWJUB0qsB9euIDt4oB1CgxLd5Y5IO6lSDiFCkxsIXj_58PDNTLWRfV-B6hYCaFbPOrF3IfkEUyfgWt2SKAy9X28IsnTG7xozdOhouP934xUR5-Ionb-qrQ0T9MNJT3f4cUa__1Vhn9k9r2KOqEdvCGwbGUocgacJH54o_vQUB9C7yhfLNz6vGsZvtpQ-PW5N8C_edCm7saNq18yRcf7grOzaZnVrWFATLFyVQFxeOAvo
In order for the authentication flow described above to complete successfully, the mobile app must be able to communicate directly with the Appian server.
Appian does not support any configuration in which Appian Mobile needs authentication cookies to reach the Appian server.
If communication between the mobile app and server is routed through an intermediary, such as a load balancer or proxy, both the request and response must remain unmodified.
Appian does not support any configuration in which Appian Mobile receives HTTP responses from a server other than an Appian server.
Appian Mobile supports two methods of restricting network access to the server: VPNs and Client Certificates.
Appian Mobile can connect to a VPN-protected server as long as the mobile device is connected to the VPN. Mobile devices can connect to a VPN at the operating system level or with a per-app VPN configured through MDM.
The Appian server can be secured behind a network gateway that issues certificate challenges. Appian Mobile allows users to import a client certificate to be used whenever a certificate challenge is received. See Client Certificate Access for more information.
Mobile Authentication Requirements