|
This page applies to Appian Cloud only. It may not reflect the differences with Appian Government Cloud. |
Note: Log Streaming is available only to customers enrolled in Professional or Signature Success Plans. The functionality described below is not included in the base Appian platform.
OverviewCopy link to clipboard
Appian Cloud environments can be configured to stream supported logs, in real time, to your own syslog receiver. Once logs are stored in a central repository, you can index, access, search, and correlate events using your existing Log Management and Security Information and Event Management (SIEM) tools.
This service operates on a push-based model, in which Appian Cloud environments are configured to send a stream of logs to your syslog receiver. Logs are forwarded in real-time as the messages are written in the Appian Cloud environment.
These logs can be further digested and aggregated by tools of your choice, such as Splunk, LogRhythm, and Elasticsearch-Logstash-Kibana (ELK) stack.
BenefitsCopy link to clipboard
With this service enabled on your Appian Cloud environment, you can integrate the information contained in the logs for a consolidated view of your enterprise operations. Some benefits of this service include:
- Simplified log management: You can easily consume your logs from a centralized location.
- Faster diagnosis and troubleshooting of your enterprise applications: You benefit from increased visibility of debugging messages. For example, you can expose these messages to Appian designers and system administrators to quickly resolve application-level incidents as soon as they are generated.
- Improved system visibility: You can assess historic performance by aggregating system metrics over time. This allows you to visualize, identify, and predict patterns in the demand of your enterprise applications.
- Integrated security analytics: You can continuously monitor for login activity to your Appian Cloud environment. By integrating with other enterprise systems, you can audit and correlate patterns in a unified platform.
SetupCopy link to clipboard
Log Streaming supports the transmission of messages to either a self-managed syslog receiver or a Sumo Logic Cloud Syslog Source.
Self-Managed Syslog Receiver (IPsec VPN Tunnel)Copy link to clipboard
The figure below shows an example of the message flow between your Appian Cloud environment and a self-managed syslog receiver in your network using an IPsec VPN tunnel.
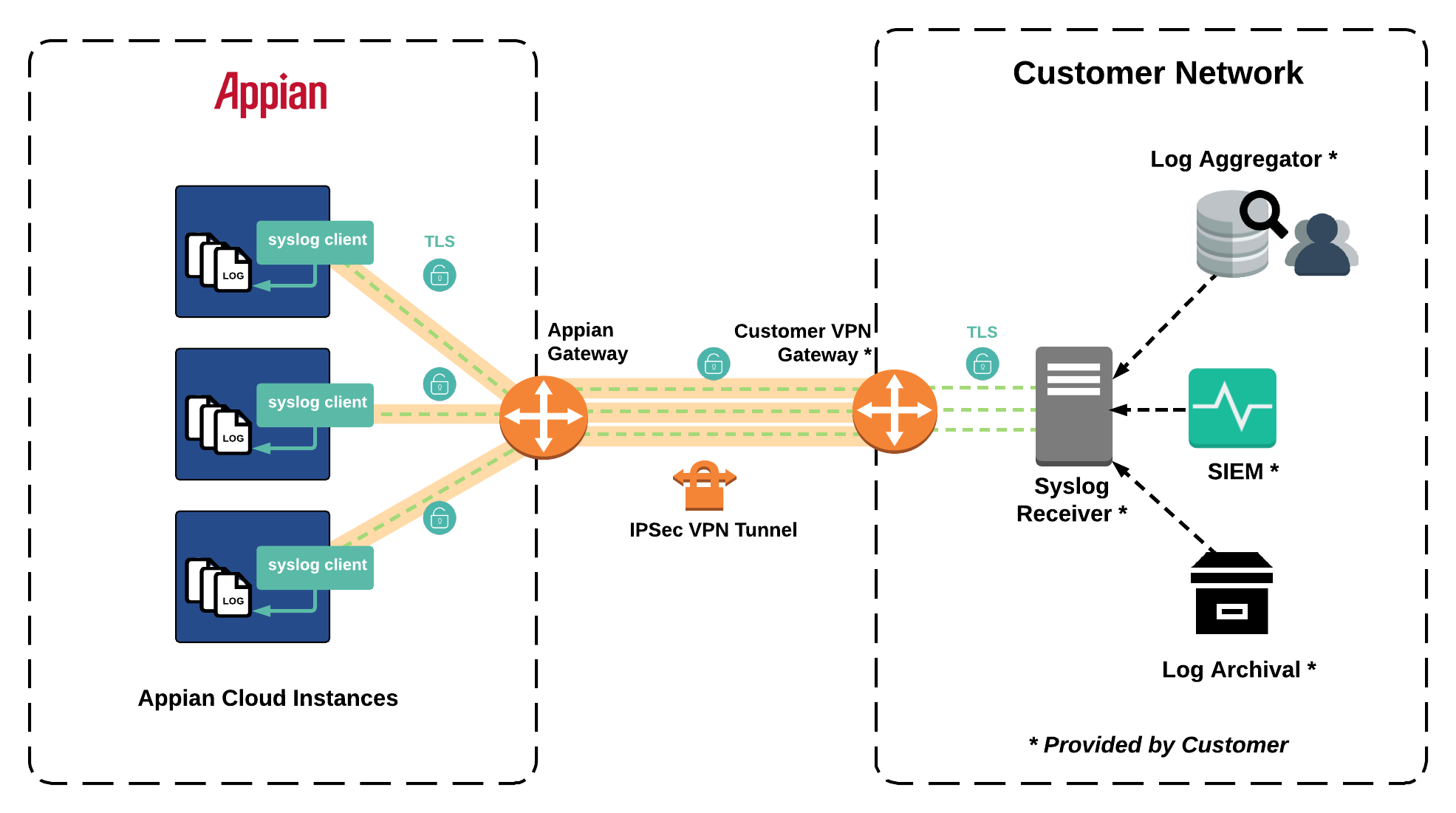
Log transmission is performed over an IPsec VPN tunnel established to your network. As an additional security layer, syslog messages can be encrypted using a TLS certificate installed on the syslog receiver that you provide. TLS encryption is enabled by default but can be disabled upon your request.
Self-Managed Syslog Receiver (AWS PrivateLink)Copy link to clipboard
The figure below shows an example of the message flow between your Appian Cloud environment and a self-managed syslog receiver in your network using AWS PrivateLink.
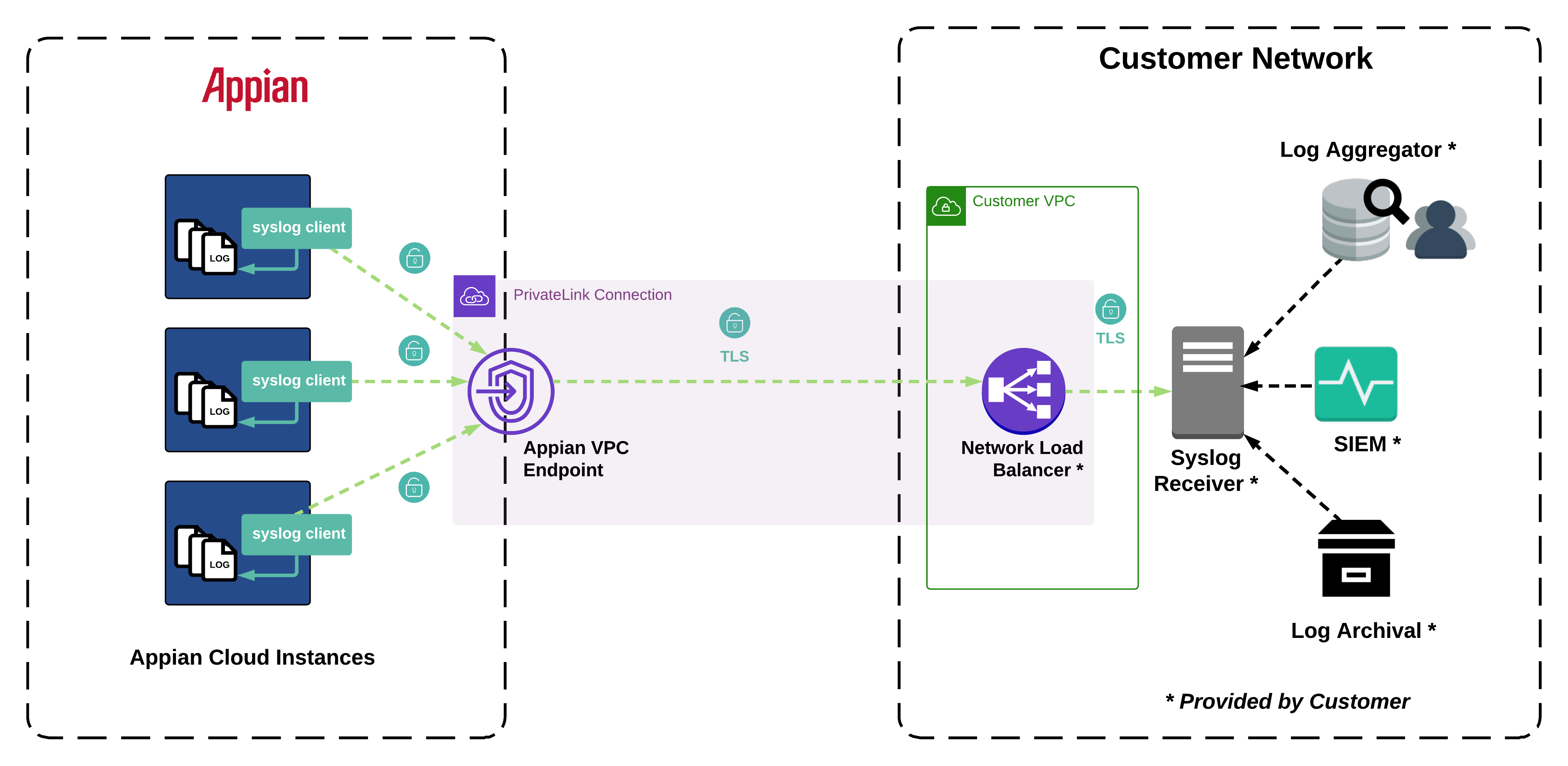
Log transmission is performed using an AWS PrivateLink connection established to your network. Syslog messages are encrypted with TLS using a trusted public CA-signed certificate that you install on your own syslog receiver.
Self-Managed Syslog Receiver (TLS 1.2)Copy link to clipboard
The figure below shows an example of the message flow between your Appian Cloud environment and a self-managed syslog receiver over the public internet using TLS 1.2.
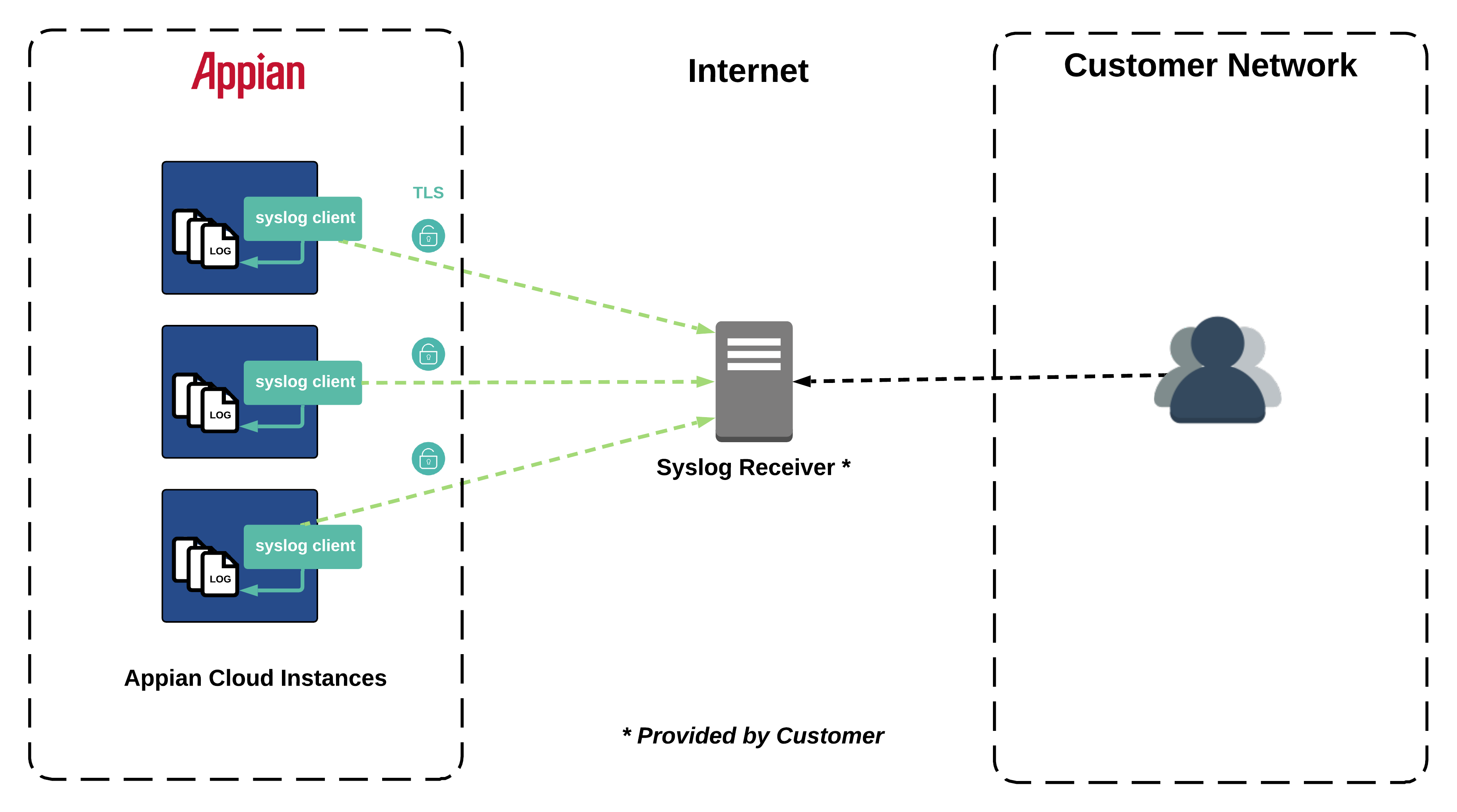
Log transmission is performed using TLS 1.2 with TCP and syslog messages are encrypted using a publicly trusted CA-signed certificate that you install on your syslog receiver.
Sumo Logic Cloud Syslog SourceCopy link to clipboard
The figure below shows an example of the message flow between your Appian Cloud instance and a Sumo Logic Cloud Syslog Source.
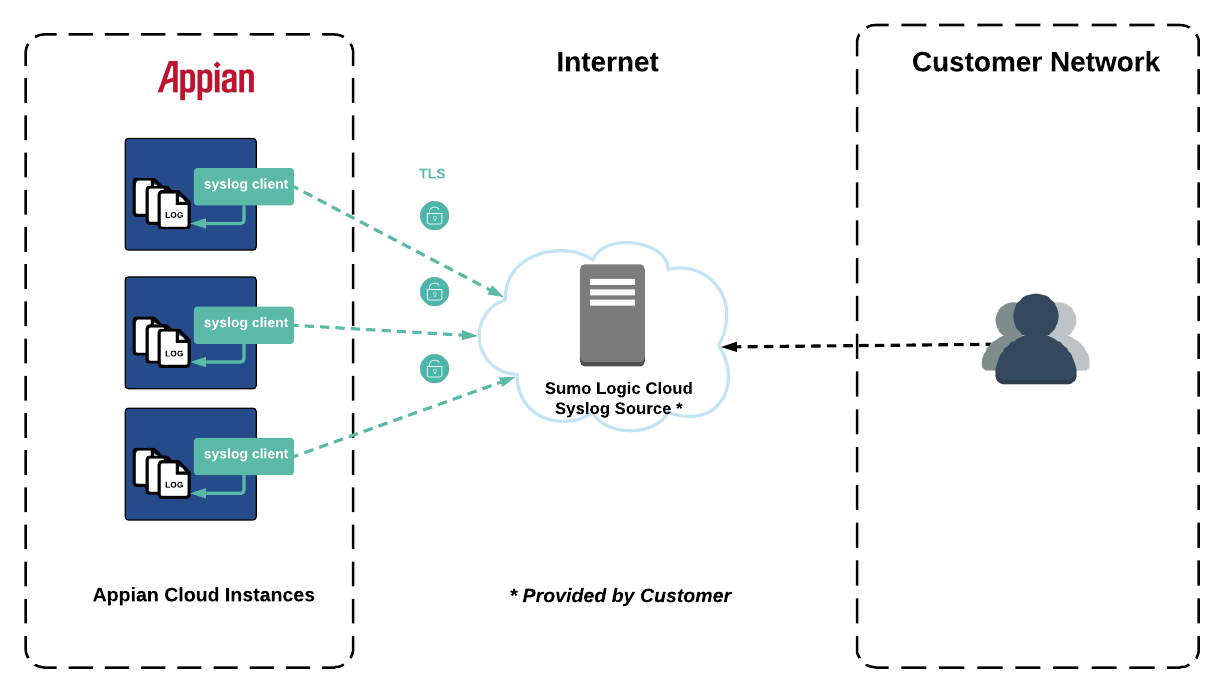
For a Sumo Logic Cloud Syslog Source, log transmission is performed over the internet and syslog messages are encrypted with TLS using the trusted public CA-signed certificate provided by your Sumo Logic deployment.
Supported logsCopy link to clipboard
The table below contains the logs to be forwarded by each Appian Cloud environment with this feature enabled. For details about the contents and frequency of the log messages, refer to the Appian Logging documentation. To add or remove logs to stream, open a Support Case.
| Log | Filename | Tag |
|---|---|---|
| Admin Console Audit | admin_console_audit.csv |
admin-console-audit: |
| Admin Console User Start Pages | admin_console_user_start_pages_audit.csv |
admin-console-user-start-pages-a: |
| AI Input/Output Activity | ai_input_output_activity.log |
ai-input-output-activity: |
| AI Usage | artificial_intelligence.csv |
artificial-intelligence: |
| Application Server | tomcat-stdOut.log |
tomcat-logs: |
| Authorization Audit | authz-audit.log |
authz-audit: |
| Autoscale Error Logs | tomcat-stdOut.log |
autoscale-tomcat-logs: |
| Blocked Files | blocked_files.csv |
blocked-files: |
| Cloud Database Audit | RDBMS-audit.log |
rdbms-audit: |
| Deletions | deletion.log |
deletion: |
| Design Objects | design_objects.csv |
design-objects: |
| Forgot Password Requests | forgot_password_requests.csv |
forgot-password-requests: |
| Group Management | group_management.csv |
group-management: |
| Logins | login-audit.csv |
login-audit: |
| Logouts | logout-audit.csv |
logout-audit: |
| Password Resets | password_resets.csv |
password-resets: |
| Perf Monitor RDBMS | perf_monitor_rdbms.csv |
perf-monitor-rdbms: |
| Perf Monitor RDBMS - Slow | perf_monitor_rdbms_slow.csv |
perf-monitor-rdbms-slow: |
| Records Usage | records_usage.csv |
records-usage: |
| Robotic Process Automation | jidoka.log |
jidoka: |
| Secure Credentials Store | secure_credentials_store.csv |
secure-credentials-store: |
| Sites Usage | sites_usage.csv |
sites-usage: |
| System metrics | system.csv |
system-metrics: |
| Task Errors | task_errors.csv |
task-errors: |
| Tomcat Access | tomcat-access.log |
tomcat-access: |
| Unscanned Files | unscanned_files.csv |
unscanned-files: |
| User Management | user_management.csv |
user-management: |
| Username Changes | username_changes.csv |
username-changes: |
| Web API Details | web_api_details.csv |
web-api-details: |
| Web API Summary | web_api_summary.csv |
web-api-summary: |
Caution: It is only possible to stream the RDBMS audit logs in a single-node or standard 3-node Appian Cloud HA configuration. Customers with other topologies where Appian and the RDBMS are not running on the same server will be unable to stream this log.
Syslog messages have the following format:
1
<PRI> <TIMESTAMP> <HOSTNAME> <TAG> <MESSAGE>
Copy
PRI: Specifies the priority of the syslog message (RFC5424)TIMESTAMP: Date and time of the message. The value will be expressed in the timezone configured on your syslog receiver.HOSTNAME: Appian Cloud instance name.TAG: Message tag depending on the log file.MESSAGE: Complete log message generated by the Appian component. Messages also contain timestamps expressed in Greenwich Mean Time Zone (GMT).
Prerequisite checklistCopy link to clipboard
| Prerequisite | Description | Organizational Role |
|---|---|---|
| Professional or Signature Success Plans Order Form | This offering is available via Professional or Signature Success Plans. | Business relationship owner |
| Update to a current Appian version | Appian Cloud environments with this feature enabled should be running a supported Appian version per the Support Policy. | Authorized Support Contact |
| Set up an IPSec VPN Tunnel, AWS PrivateLink, or TLS 1.2 connection (Only required for self-managed syslog receivers) | For self-managed syslog receivers you are required to establish an IPSec VPN Tunnel, AWS PrivateLink, or TLS 1.2 connection to your network which will allow connectivity to your syslog receiver. Both Static and Dynamic IPSec VPN tunnels are compatible with Log Streaming. Refer to Cloud VPN Integration documentation, Dynamic VPN Integration documentation, or Cloud PrivateLink Integration documentation for detailed steps. | Network Administrator / Authorized support contact |
| Set up syslog receiver |
For Sumo Logic Cloud Syslog Source:
|
Server/Network Administrator |
StepsCopy link to clipboard
Once all prerequisites have been completed, you can follow these steps to enable log streaming in your Appian Cloud environment:
- Open a Support Case requesting for enabling this service in your Appian Cloud environment. Provide the following details:
- Syslog receiver target
- For self-managed syslog receivers using IPsec VPN, you will provide a private IP address or hostname that is part of your private network space.
- For self-managed syslog receivers using AWS PrivateLink or TLS 1.2, you will provide the hostname of your syslog receiver.
- For Sumo Logic, you provide the endpoint hostname.
- Port
- Token (Sumo Logic only). You need to provide the token that is generated during the setup process. This information should be provided to Appian Support over the phone or in-person to be consistent with good security practices.
- Syslog receiver target
- Appian Support will schedule a maintenance window and deploy the necessary configurations.
- After the maintenance window, your Appian Cloud environment will start forwarding logs to your syslog receiver.

